Quick Overview
IAC tools let you define infrastructure in code, so every change is versioned, reviewed, and stored in Git, just like application code. For platform, QA, and release teams, that means better traceability, fewer environment errors, and more reliable deployments.
In this article, I explain how to choose the right Infrastructure as Code tool based on your cloud, Kubernetes, and security needs, and where Golive fits into helping teams coordinate shared environments more reliably.
Infrastructure as Code (IaC) has changed how teams provision infrastructure, but visibility and coordination still lag behind. Even with tools like Terraform or Pulumi in place, teams often run into testing delays, configuration drift, or overlapping usage of shared environments. IaC solves repeatability, but it doesn’t manage scheduling, ownership, or environment conflicts.
These issues come up across platform, QA, and release teams because collaboration around environments is rarely tracked or centralized. Today, IAC adoption has become standard across DevOps, release, and platform teams. And if you're just starting out with IAC tools, you've probably read our IAC guide that explains what it is and why it matters.
This post is the next step. It's the "how to choose" guide. I'll discuss the practical side of picking the right IAC tool, based on your cloud stack, Kubernetes usage, and security needs.
And because there's no one-size-fits-all answer, I'll show where each tool fits best. Whether you're running hybrid infrastructure or going all-in on GitOps, you'll leave with a clear idea of what works for the team.
The Criteria: What Matters When Choosing an IAC Tool
Before you get into the Infrastructure as Code tools comparison, let's look at how I'll evaluate each tool.
Evaluation Criteria:
Cloud support: Does it work across providers, or is it tied to one vendor?
Kubernetes support: Does it support K8s natively, or through plugins?
Security: How does it handle secrets, policies, and access controls?
Ease of use: What's the learning curve like? Is the syntax beginner-friendly?
Community and ecosystem: Are there modules, plugins, and docs to lean on?
Scalability and performance: Can it handle large, complex environments?
CI/CD integration: Does it work well with GitOps and modern pipelines?
This gives a clear, fair way to compare tools, based on what actually matters when you're deploying infrastructure at scale.
IAC Tools Compared by Key Capabilities
Take a look at this IAC tools comparison table.
Tool | Cloud Support | Kubernetes Support | Security Features | Ease of Use | Integrations | Best For |
|---|---|---|---|---|---|---|
Terraform | Multi-clouds | Strong via providers | Sentinel, Vault | Moderate | Strong | Enterprises, multi-cloud infra |
Pulumi | Multi-cloud | Native SDKs | Code-based policies | Dev-friendly | Good | Dev teams, app + infra teams |
AWS CDK | AWS only | Yes | IAM, KMS | Dev-friendly | AWS-integrated | AWS-heavy teams |
Crossplane | Kubernetes-native | Native | OPA | Steep | Modern | Kubernetes-first orgs |
Ansible | Broad | Limited | Vault | Easy | Legacy + new | Hybrid infra, ops teams |
Helm | N/A | Native (charts) | RBAC, Secrets | Simple | Kubernetes | K8s app deployment |
Where Each Infrastructure as Code Tool Fits
Now that you've seen the evaluation criteria, here's what each tool does well, and when you might want to pick something else instead.
Terraform
Use Terraform when you want one tool to manage infrastructure across multiple cloud providers. It's declarative, widely adopted, and backed by a massive module ecosystem.
If consistency and predictability matter more than writing logic-heavy configurations, Terraform makes sense.
It keeps things simple and aligned across teams. You won't be writing fancy conditions, but that's kind of the point.
Pulumi
Amongst IAC tools, Pulumi is the one that gives you full programming power. You can define infrastructure in TypeScript, Python, or Go, and organize it with real functions and abstractions.
It's great when your infrastructure mirrors your application.
But that flexibility means code reviews get heavier. Pulumi's a strong fit for teams already used to engineering workflows, and having a visual layer like Golive helps make those changes visible beyond just the Git diff.
Golive shows what’s deployed, who made changes, and when, so your team stays aligned, even as infrastructure evolves.
AWS CDK
If you're fully on AWS, CDK can save you time. It compiles your code into CloudFormation, which means the full power of AWS with a cleaner developer experience.
If you don't need multi-cloud, it keeps things moving fast. No need to translate between YAML and your app codebase.
Ansible
Ansible is still a go-to for procedural tasks, hybrid setups, and fast fixes. No agents, no state files, just a command and a playbook.
I often recommend it for teams with SSH access and tight turnaround times.
Crossplane
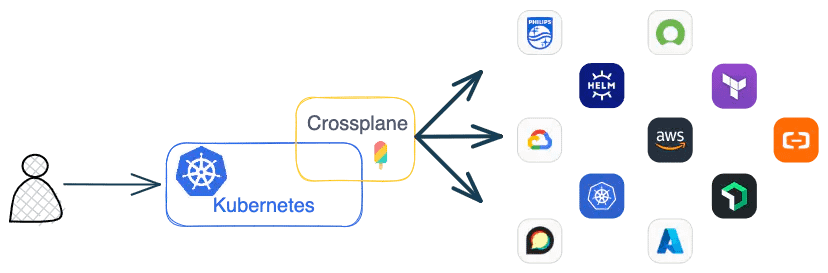
Crossplane fits right into Kubernetes-native workflows. If your team is already using GitOps, you can extend that same model to cloud infrastructure, right from inside your cluster.
It's declarative and built on CRDs, which makes it powerful once you're used to the patterns. But it does have a learning curve, and you'll need some experience with Kubernetes controllers.
If that's already your world, Crossplane will feel like a natural extension for sure.
Use Cases: Matching Tools to Scenarios
When teams ask me which IAC tool to pick, I always say: it depends on what you're dealing with day to day.
Your cloud stack, how your team works, the kind of infrastructure you manage, those are the real decision-makers.
So instead of listing features again, let's look at the kinds of problems I've seen teams run into and which Infrastructure as a Code tools helped solve them.
Aws-Only, Fast-Moving Teams
If you're all-in on AWS and tired of copy-pasting YAML, use AWS CDK.
It lets you define infrastructure in Python or TypeScript and compiles it to CloudFormation behind the scenes. It feels like writing app code, and it works best when your whole stack lives in AWS.
Kubernetes-First With GitOps
You've got apps running in Kubernetes, but infra's still managed in Terraform or scripts. That gap breaks GitOps flow.
Crossplane brings cloud infra into your cluster using CRDs. Prefer SDKs? Pulumi lets you write it all in real code.
Both tools help you manage everything in Git, just like app changes.
Hybrid Setups With SSH Access
Not everything runs in the cloud.
If you're configuring VMs or patching servers, Ansible still does the job. It's agentless, YAML-based, and runs over SSH.
I've seen teams roll out updates across dozens of environments without touching a cloud console once. But when multiple teams work in the same environments, such as Dev, QA, and Ops, it gets hard to stay aligned.
Tests might run on outdated configurations or overlap with ongoing patches. Apwide Golive helps prevent that.
It lets teams book environments, track usage, and publish schedules directly in Jira and Confluence. It keeps everyone informed and your shared setups under control.
Since Golive works alongside any IaC tool, you get visibility across environments without changing how you define them. That means fewer overlaps, better planning, and a shared understanding of what’s live.
Multi-Cloud Teams Needing Stability
Managing AWS, GCP, and Azure? Terraform gives you a single language to describe it all. It's declarative, versioned, and has a huge module registry.
When I need reliable, cross-provider infra that just works, this is what I reach for.
Dev Teams Writing Infra as Code
If you need logic-heavy infrastructure tied to app behavior, Pulumi gives you that flexibility.
You can use familiar languages, create abstractions, and build complex environments with real programming power.
Security and Policy Considerations
I've seen great setups fall apart because secrets weren't handled properly, or no one caught drift until it broke something.
So let's look at how the main IAC tools deal with secrets, policy enforcement, and keeping environments auditable.
Terraform integrates with Vault for secrets and uses Sentinel for policy checks. It also flags drift with every plan.
Pulumi supports SOPS and cloud-native managers. Policies aren't built-in, but you can handle them with code and CI.
AWS CDK relies on IAM, KMS, and CloudFormation's drift detection. You get fine-grained control, but it's AWS-only.
Ansible uses its own Vault and can plug into external managers. No state tracking means drift checks need extra work.
Crossplane manages everything through Kubernetes. OPA and Kyverno handle policies, and built-in controllers monitor drift continuously.
Across all IAC tools, secrets handling and auditability vary, so pick one that fits your compliance needs.
Tool Ecosystem Notes
Terraform has a deep registry of modules you can reuse or customize to fit your deployments.
Helm works well alongside tools like Terraform or Crossplane
Pulumi and CDK have SDK-based modularity, though reuse is more manual
Final Thoughts: Choosing the Right IAC Tool for Your Team
There's no one IAC tool that works for everyone, and that's the point. The right choice for infrastructure as code tools depends on your team's skillset, cloud stack, and security approach.
I recommend starting small. Try one or two IAC tools on something simple, like an S3 bucket or database, and see how it fits your process.
Pay attention to how reviews and visibility work. If you're still learning the basics, check out our IAC guide. What matters most is versioning, review, and visibility. Once that's in place, the rest falls into place more easily.
Key Takeaways
- Match tools to team and cloud stack
- Start with one small project or resource
- Terraform and CDK suit predictable infrastructure
- Pulumi and Crossplane support dynamic workflows
- Review security, secrets, and drift handling
- Use Git for visibility and traceability
- Read the IAC guide for foundations