Deploying new software for remote teams can be a challenging task. It's important to approach the deployment process with a well-thought-out plan that takes into account the unique challenges of working with a remote team.
This includes planning, testing the software, scheduling the deployment, providing user training, and continuously monitoring the software's performance. Security is also a key concern, and measures such as secure remote access and regular security audits also need to be implemented.
With the right approach, it's possible to successfully and securely deploy new software for remote teams, and in this article, we’ll delve into the details of this process.
Creating a Plan
It’s the first step and the most critical step of the entire deployment process that you must carry out very carefully. While the exact layout and specifics of the plan will depend on your organization’s unique needs, the following are some general guidelines that you can follow.
- Summarize Your Deployment Goals
Summarizing the deployment goals means creating a complete picture, showing what the entire deployment process will look like. This initial summary will lay out the scope of deployment and define the parameters for the project schedule.
- Create a Deployment Schedule
The next step is to create a deployment schedule that outlines the specific steps and timeline for deploying the new software. It should include information on when the new software will be deployed, who will be responsible for different tasks, and what resources will be needed.
- List Deployment Requirements
Deployment requirements refer to the specific conditions or elements that need to be in place before the software can be deployed. It's important to identify and meet these requirements in order to ensure a smooth and successful deployment.
Here’s a list of important factors that you must keep in mind while listing down deployment requirements.
- Create a Deployment Communication Plan
A clear communication plan is essential for a successful deployment. It’s about identifying who needs to communicate with whom, how often, and through what means. Here are some tips that you can use for this purpose.
- Identify Key Stakeholders: This includes the project manager, development team, QA team, operations team, and any other relevant parties.
- Establish Communication Channels: Determine the best means of communication for each stakeholder, such as email, instant messaging, phone, or video conferencing.
- Ensure Security: For teams working remotely, it is important to establish a secure communication channel using a reliable VPN (Virtual Private Network) to ensure the confidentiality and integrity of the data being transmitted.
- Use Centralized Platform: Use a centralized project management tool, such as Jira for deployment management, to keep track of tasks, milestones, and progress. It’ll ensure that everyone has access to the most up-to-date information. You can also use Golive to integrate other tools you’re using with Jira to streamline deployment processes.
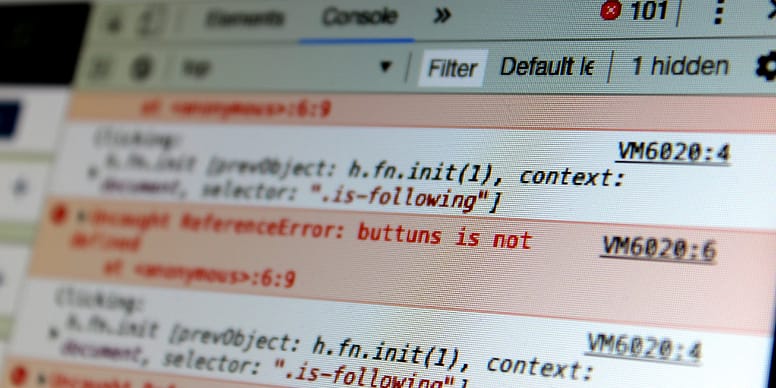
Perform Rigorous Software Testing
Rigorous software testing is a crucial step in ensuring that the code being deployed is functional and works as intended while maximizing velocity and minimizing bugs. You can break down the testing phase into the following steps:
- Test Verification
Test verification helps you mitigate the risks associated with new code. Developers should start by writing tests for their software to confirm that it does what it is supposed to do. This can be done by running automated tests after every commit using tools like git hooks or CI/CD pipelines.
- Manual Functionality Verification
While automated testing can be efficient, not all testing lends itself to automation. Therefore, it’s important to invest time in manual testing. This can be done by building effective unit tests and performing high-quality manual testing.
Tip: You can use tools like Testim test automation to perform automated end-to-end testing.
Carry Out the Deployment
Deployment is the process of moving a software application from a development environment to a production environment. This step ensures that the application is ready to use.
This process can be manual or automated, depending on the application, tools, and infrastructure you're dealing with. Manual deployment involves copying the application's files and configurations to the production server.
Automated deployment involves using a deployment tool, like the ones discussed above, or a script to automate the process of deploying the application. This method is more efficient as it eliminates the need for manual intervention and reduces the risk of errors.
After deployment, it's essential to perform post-deployment testing to evaluate the software functionality in the production environment. This process includes monitoring the application's performance, user feedback, and fixing any bugs that are found.
Offer User Training
Training your users enables them to effectively use and utilize the newly deployed software. It can lead to increased satisfaction and productivity.
Here are some key elements to consider when training your users:
- Define the Objectives: Clearly outline the goals and objectives of the training, and what the users should be able to accomplish by the end of it.
- Choose the Right Format: Decide on the format that will work best for your users and goals. This can include in-person training, online tutorials, webinars, videos, or written documentation.
- Create Engaging and Interactive Content: Use a variety of media and interactive elements to keep the users engaged and make the training more effective. Make sure that you use videos and infographics as they’re more engaging than text.
- Follow Up and Provide Support: Provide ongoing support to the users to ensure that they can fully utilize and benefit from the product.
- Update the Training Continuously: As your product evolves, ensure that the training material is also updated to reflect the new changes.
Ensure Continuous Monitoring
Continuous monitoring will help you maintain the integrity and security of your system. It involves analyzing system logs, network traffic, and other data sources regularly to identify potential security threats and vulnerabilities.
Here are some key components of continuous monitoring:
It’s also important to regularly audit the overall security controls of the system to protect it from cyber threats.

Have a Contingency Plan
A contingency plan is a backup plan that outlines the steps to be taken in case of an unexpected event. It includes anything from a natural disaster, to a security breach, to a system malfunction.
It’ll allow you to respond quickly and effectively to any unexpected issues, minimizing the impact on your remote team and ensuring that your software deployment remains secure. The plan should outline a clear and detailed set of instructions on what steps to take if an unwanted event occurs.
Additionally, it’s also important to involve all relevant stakeholders in the development and implementation of the contingency plan, including both technical and non-technical team members. It’ll help you make sure that everyone is aware of the plan and understands their role in implementing it, which can be critical in case of an emergency.
You should also regularly review and update your contingency plan to ensure that it remains relevant and effective. This involves conducting regular risk assessments, testing the plan, and making any necessary adjustments based on feedback from your team.
Bottom Line
Deploying new software for remote teams can be a complex and challenging task, but with the right approach and tools, it can be done securely and efficiently. The key is to plan ahead, communicate effectively, and be prepared for any issues that may arise.
We hope that this guide has provided valuable information and insights to help you successfully deploy new software for your remote team. It’ll help you ensure that your team has the tools and resources they need to be productive and successful, no matter where they are located.
