Quick Overview
Incident Management in test environments is often overlooked, but it's one of the key factors in delivering reliable software without delays. This guide explains what incident management looks like outside production, how to define and handle incidents, and why visibility matters more than perfection.
In a previous role at a large advertising tech company, I observed what appeared to be a well-organized incident management setup. There was a central Slack channel with bots integrated to PagerDuty, New Relic, Jira, and GitHub. Every incident had a dedicated Zoom war room, automated post-mortem templates, and a dashboard tracking incident volume, root cause actions, and resolution metrics. It seemed flawless.
But it wasn't. Underneath the surface, small incidents were happening in teams with low visibility. One day, I joined a team running a business-critical ETL (Extract, Transform, Load) pipeline. When I asked, "How do you know something went wrong?" the developer said, "I check the email reports every morning." That moment revealed what no dashboard showed: incidents were happening, but they weren't being managed.
This guide compiles what I learned from that experience. It's for you if you're managing test environments, building QA processes, or working to improve how your team handles issues before they reach production.
The Hidden Cost of Poor Environment Management
When test environments fail unpredictably, teams lose significant time and face cascading consequences. According to our Software Release Management Essential Guide: "Release management involves the strategic process of planning, designing, testing, deploying, and overseeing software releases". When this process is compromised by poor environment management, it leads to inadequate testing, delayed deployments, and disrupted release coordination. These issues manifest in extended cycle times, missed deadlines, and reduced team efficiency, exactly what our ETL pipeline team experienced.
The financial impact is more severe than most organizations realize. Research from the Enterprise Management Associates (EMA) reveals that the true cost of inefficient environment management for the average enterprise is $1.4 million per year (for only 76 production releases per year), as detailed in How Much is Inefficient Environment Management Costing You?. For organizations managing an average of 188 environments, potential savings exceed $128,000 annually through proper environment management practices.
Without proper incident management, what should have been routine data processing turned into daily fire-fighting. Each silent failure cascaded into delayed testing cycles, missed release windows, and frustrated stakeholders. The real includes the immediate downtime, the accumulated technical debt from rushed fixes, and the erosion of team confidence in our delivery process.
This is why incident management in test environments isn't optional. It's the difference between controlled, predictable releases and chaotic scrambles to meet deadlines. As we discovered, you can't manage what you can't see, and you can't improve what you don't measure. Modern DevOps practices emphasize the importance of treating test environments with the same rigor as production systems. This includes implementing proper incident response workflows, establishing clear escalation paths, and maintaining visibility across all stages of the delivery pipeline. For comprehensive strategies on building resilient incident response processes, explore DevOps best practices for incident response.
What Is Incident Management in Test Environments?
In production, an incident is usually loud. Users complain, alerts fire, revenue drops. In test environments, it's quieter but equally disruptive, yet often goes unnoticed until it's too late. This silent nature is precisely what made our ETL pipeline failures so damaging. While production incidents scream for attention, test environment incidents whisper their way into release delays and technical debt.
An incident in a test environment might mean:
A test environment is down or unreachable
A CI pipeline fails unexpectedly
Test data is corrupted or missing
A 3rd-party sandbox is offline
These don't affect customers directly, but they delay releases, create rework, and frustrate developers and testers. They can also be extremely expensive financially. In my experience with the ETL pipeline, one of the invisible test environment issues cost hundreds of dollars per deployment because the system was re-downloading images unnecessarily due to corrupted test data, a silent failure that fell squarely into the "test data corrupted" incident category. Unlike production incidents that announce themselves loudly, test environment failures whisper their way into release delays and unexpected costs.
The key difference: in test environments, you must define what qualifies as an incident. This was one of our biggest challenges with the ETL pipeline. A failed job didn't crash a service or trigger obvious alerts; it silently caused stale data that only became apparent through manual inspection. We had to redefine what "failure" meant in our specific context, establishing clear criteria for when a test environment issue warranted incident response versus routine troubleshooting.
ITIL 4 Principles Applied to Test Environments
ITIL defines incidents, problems, and changes with clear roles and flows. These principles work outside production, too, if adapted:
Define SLAs/OLAs for test environments
Appoint someone responsible for environment health
Run post-incident reviews even when users aren't affected
Use metrics: Mean Time to Acknowledge, Mean Time to Resolve, Repeat Incident Rate
ITIL lifecycle stages can be applied to test environments with slight adjustments. The core stages (identification, logging, categorization, prioritization, diagnosis, resolution, and closure) remain valuable. In our ETL case, we used these stages to track data pipeline incidents: detecting failures, logging impact, diagnosing the root cause, and closing with a documented fix. Closure meant recovery plus ensuring data consistency and noting long-term improvements.
We also looked at how recurring issues in non-prod environments could be tracked using Problem Management techniques. In our case, many failures in ETL weren't new. They were recurring failures due to a lack of proper alerting and unclear ownership.
The ITIL 4 Release Management framework emphasizes the importance of integrating release management with other ITIL practices like Change Control, Incident Management, and Problem Management. As noted in the comprehensive guide, "Release management is integrated with other ITIL practices like Change Control, Incident Management, and Problem Management. This integration fosters collaboration and helps refine the release management process based on insights and feedback from these related areas." This integration is particularly valuable in test environments where incident patterns often reveal underlying release process gaps that need systematic attention.
While this guide covers ITIL fundamentals, implementing a formal ITIL Incident Management framework requires understanding specific processes, role definitions, and service level agreements tailored for test environments. Similarly, addressing recurring issues systematically involves Problem Management techniques that go beyond individual incident resolution to identify root causes, implement permanent fixes, and establish metrics for preventing future occurrences.
ITIL can and should be applied to non-production environments, even if your team runs Agile. Discipline and visibility don't conflict with flexibility; they support it. The structured approach of ITIL provides the foundation that allows Agile teams to respond quickly while maintaining accountability and learning from incidents.
Agile & DevOps Approaches to Incidents
Agile teams often treat incident resolution as part of sprint work. And rightly so. Environment issues can be blockers and should be visible and actionable within the same delivery rhythm. Teams that proactively flag broken test environments as sprint blockers tend to resolve them faster and document systemic issues in real time.
In our case, the ETL failures became sprint risks that required proactive management. We treated each critical issue as a backlog item, tracked RCA tasks, and prioritized repeated failures for systematic resolution. When you embed incident resolution into the sprint cycle, you create dedicated space for prevention alongside repair.
From a tooling perspective, we used Jira to log environment-related incidents and linked them directly to related tickets, test failures, and RCA items. Slack updates helped keep stakeholders informed, while Zoom links for war rooms were embedded into Jira tickets for fast coordination.
What we learned from DevOps:
CI failures are incidents
Automation must include failure detection
Post-mortems help identify systemic gaps
Use pipelines and observability tools as early warning systems
We also adopted the "stop the line" approach: if a test stage failed, we paused downstream work until we understood why.
📌 Here's a comparison of how incidents typically play out across methodologies:
Trigger | Agile | DevOps | ITIL 4 |
|---|---|---|---|
Standup blockers | ✅ Declared by team | 🔁 Detected by tools | 🛠 Logged by ITSM |
Pipeline fail/alerts | ⚠️ Raise ticket | ✅ Alert + action | 🚨 Log + categorize |
User/system report | 🧪 Tester flags | 📈 Metrics & monitors | 📝 Recorded formally |
Response | 🧩 Team swarm | 🧠 On-call + automation | 📋 Escalation paths |
Closure | ⏱ Sprint completed | ✅ Green pipeline | 📄 Closed in system |
Typical Incidents in Test Environments
Test environments fail in many subtle ways that can have outsized effects on delivery. We experienced this first-hand with our ETL pipeline project.
First, environments may become unavailable without any notice. Sometimes due to infrastructure updates, expired credentials, or broken dependencies. In our case, the environment would seem "available" but silently fail to process key data, leading to inaccurate downstream reporting.
Second, mismatched or missing test data was a regular issue. Because the pipeline depended on fresh datasets, any corruption or outdated input silently invalidated the output. These failures weren't caught by automated tests and were only noticed through manual checks, often too late.
Third, we encountered disk space exhaustion in our test environment. Our test environment used a small, fixed-size disk since it was "just for testing." However, as our automated tests ran repeatedly, they continuously downloaded images without cleanup. Eventually, the disk filled up completely, causing all tests to fail silently.
We also experienced pipeline failures in our CI/CD pipeline, especially when build agents were overwhelmed or misconfigured. These failures didn't always bubble up visibly. Without integrated alerting, the only signal was missing output.
What made the disk space issue particularly problematic was its gradual nature; tests would slow down progressively before failing entirely. We had to investigate system logs to discover the root cause, then implement disk usage monitoring and add technical debt items for automated cleanup and elastic storage solutions.
Finally, external dependencies like a third-party marketing API or sandbox could go offline without notice. One morning, we discovered that thousands of records weren't processed because the external system returned a silent timeout for several hours.
At the time, our only detection method was a manual scan of a daily email report. That wasn't enough. We responded by creating a model to classify and respond to incidents in our test environment:
We defined failure types relevant to our pipeline: data mismatch, job interruption, third-party timeout, etc.
We set thresholds for alerting, so not every glitch triggered a fire drill, but critical issues never went unnoticed.
We automated detection using New Relic and custom scripts that monitored key points in the ETL flow.
This improved both our response time and team confidence. Instead of relying on instinct or manual checks, we had real visibility and control.
Here's a typical flow:
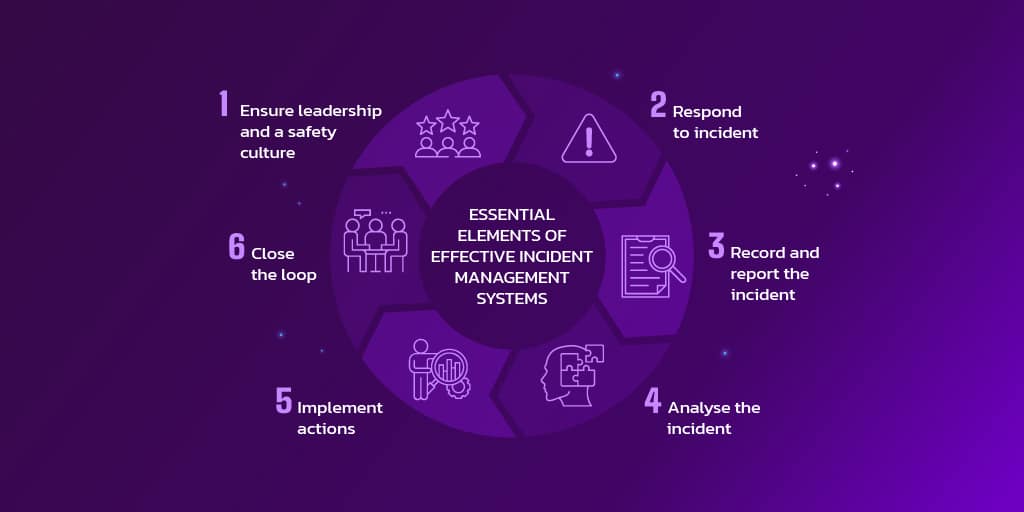
Building a comprehensive incident management process workflow involves more than just knowing the steps. It requires establishing clear detection mechanisms, defining triage criteria and priority levels, creating communication templates for different stakeholder groups, setting resolution timeframes, and designing review processes that feed back into prevention strategies. Each step needs specific procedures, responsible parties, and measurable outcomes.
How to Structure Incident Management in TEM
To manage incidents well, we had to develop a clear structure, especially after seeing how fragile things could be when dependent on manual oversight. Here's how we approached it in the context of our ETL pipeline team:
Ownership was the first gap we addressed. Initially, no one felt fully responsible for the pipeline's health. If something went wrong, it wasn't clear who should act. We created a clear ownership model: one person was responsible for detection and triage, while another oversaw incident resolution and communication. This eliminated confusion and delays.
Logging was also inconsistent. Before, the only log was the developer's memory of what the email report looked like the day before. We introduced a simple template that captured what failed, when, how it was detected, and who acted. This gave us structure for both real-time response and post-mortem clarity.
Triage became a priority once we started logging properly. Not every alert was worth waking up for, but some needed immediate action. We built simple logic to assign priority levels based on downstream impact, data volume, and timing (for example, before a marketing campaign).
With limited resources, we had to be smart about workarounds vs. full resolution. Sometimes we re-ran failed jobs manually to unblock downstream teams, even before we fully understood the root cause. Other times, we paused everything to rebuild a broken step.
Escalation rules were a blind spot. We made sure incidents that involved data exposure, external APIs, or customer reports were automatically escalated to senior staff. That structure helped us avoid silent failures with real business impact.
We also formalized Post-Incident Reviews (PIRs). Initially, we only talked about big outages. But we soon realized that recurring small failures were just as damaging. We scheduled PIRs for repeat incidents and kept them short and actionable.
To measure progress, we tracked a few key KPIs:
- Mean Time to Resolve (MTTR): How long from detection to fix
- Incident Volume: How many incidents per month
- Post-mortem coverage: How many incidents had follow-up documentation
- Repeat Incidents: How many problems happened more than once
🧰 Your Incident Response Toolkit
Here's what helped us most:
- Monitoring: Custom scripts and New Relic metrics
- Logging: Clear logs and Jira issue links
- ChatOps: Slack alerts, Jira notifications, and Zoom war rooms
- Templates: Incident checklist, triage form, and PIR document
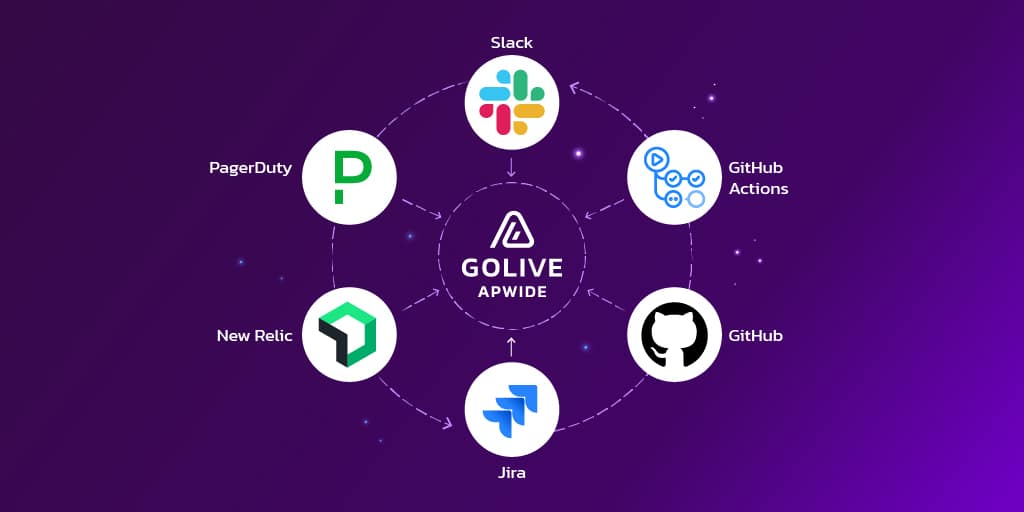
Tools That Support Visibility
Good tooling supports process, but doesn't replace it.
Tools we used:
Slack + bots for alerts
PagerDuty / Opsgenie for on-call
New Relic for observability
Jira for ticketing and follow-up
Apwide Golive for environment status and scheduling
GitHub Actions for early detection
Zoom war rooms linked directly from incident tickets
Using Jira for incident management goes beyond basic ticketing. It involves creating custom issue types for different incident categories, setting up automated workflows that route tickets based on severity and impact, configuring stakeholder notification rules, and establishing incident linking strategies that connect related issues, test failures, and follow-up tasks. Proper Jira configuration can transform incident response from reactive scrambling to organized, trackable resolution processes.
We also built a dashboard tracking:
Incident volume
Post-mortem completion rate
Follow-up item completion
Selecting incident management software requires careful evaluation of features like automated alerting capabilities, integration ecosystems, reporting and analytics depth, scalability for growing teams, and pricing models that fit different organizational sizes. The modern landscape includes both established enterprise solutions and emerging tools designed specifically for DevOps and cloud-native environments. Key considerations include API compatibility, mobile access, multi-tenant support, and the ability to handle both traditional ITSM workflows and modern ChatOps approaches.
Building on the KPIs we mentioned earlier (MTTR, incident volume, post-mortem coverage, and repeat incidents), effective incident management requires robust monitoring and reporting capabilities that provide real-time visibility into system health and historical trend analysis. The most critical aspect is establishing incident management KPIs that align with your team's specific goals - whether that's reducing mean time to resolution, improving first-call resolution rates, or tracking customer satisfaction scores post-incident.
Real-World Examples & Use Cases
A flawless setup hiding critical gaps
In the advertising tech company, we had everything that looked like best-in-class incident management: Slack bots integrated with PagerDuty, New Relic dashboards with custom alerts, automated Zoom war room creation, and Jira workflows that routed incidents based on severity. The central platform team had spent months building this sophisticated system, complete with escalation matrices and automated post-mortem templates.
But the reality was different. While the main production services were well-covered, dozens of smaller teams operated in isolation. The Tech Marketing team I joined was a perfect example: they had business-critical data processing running daily, but no connection to the central incident management system. When their jobs failed, no alerts fired. When data became corrupted, no dashboards showed red. When external APIs timed out, no war rooms opened.
These teams weren't deliberately excluded; they simply weren't onboarded. The central system was built for the "big" services, the customer-facing APIs and core platforms. Smaller teams with batch jobs, data pipelines, and supporting services were left to build their own detection methods, which often meant manual checks and tribal knowledge.
The wake-up call came during a quarterly business review when the marketing team reported that three weeks of campaign data was incomplete. Investigation revealed that our ETL pipeline had been silently failing for days, re-processing the same datasets while new data accumulated unprocessed. The financial impact was significant, affecting both reporting accuracy and cloud compute costs through redundant processing.
Key lessons learned:
The solution required both technical and organizational changes. We created simplified incident declaration workflows for smaller teams, built lightweight monitoring that could be deployed quickly, and established "incident ambassadors" who helped bridge the gap between central tooling and team-specific needs. Most importantly, we changed our definition of incident management success from "how well we handle reported incidents" to "how well we ensure all critical incidents get reported and handled appropriately."
ETL pipeline depending on a daily email
The ETL system was critical for marketing, yet had no automation or observability. Failures were caught manually. After defining what "failure" meant in that context, we implemented monitoring and created a lightweight incident declaration system.
Outcome: We moved from reactive fire-fighting to proactive detection.
From Reactive to Preventive: Learning from Incidents
Incident Management in test environments becomes more effective when you shift from reactive to preventive thinking. Incidents are useful if you learn from them. Here's how:
Conduct post-incident reviews, even in non-prod
Track patterns and recurring causes
Build a knowledge base of previous incidents
Automate recovery where possible
Share lessons across teams
Over time, this becomes a maturity model:
Ad-hoc incident handling
Centralized visibility
Defined ownership and metrics
Automation and dashboards
Preventive culture
Conclusion: Why This Matters
Incident Management extends far beyond production environments. Most issues originate earlier in the development cycle, making test environments your crucial first line of defense.
When you manage test environments with discipline, you gain faster releases, fewer delays, happier testers, and more reliable software. The investment in proper incident handling pays dividends in reduced stress, clearer accountability, and predictable delivery timelines.
Ask your team today: How do we know when something fails? If the answer involves someone manually checking, you have work to do.
Key Takeaways
- Visibility is the foundation of resolution
- Define incidents based on your environment's context
- Onboard all teams into your incident process
- Use real metrics to improve, not just to report
- Balance tools with process and culture